Secure Your Software Supply Chain
Embedded systems today are highly complex and combine a plethora of software services from various suppliers with open-source software which leads to a complex software supply chain. The blind trust in third-party software tremendously increases the risk for cyberattacks, as impressively shown by recent attacks that target the software supply chain.
The SANCTUARY Zero-Trust Platform is an all-in-one software solution that protects your embedded product against state-of-the-art cyberthreats. By combining virtualization technologies with the security guarantees of trusted computing, the ZTP achieves a strong isolation of third-party and open-source software on your product, removing the need to trust software that was not developed by your team. With this, the ZTP is the first solution that brings the zero-trust concept to embedded devices.
Replace Blind Trust with Explicit Trust
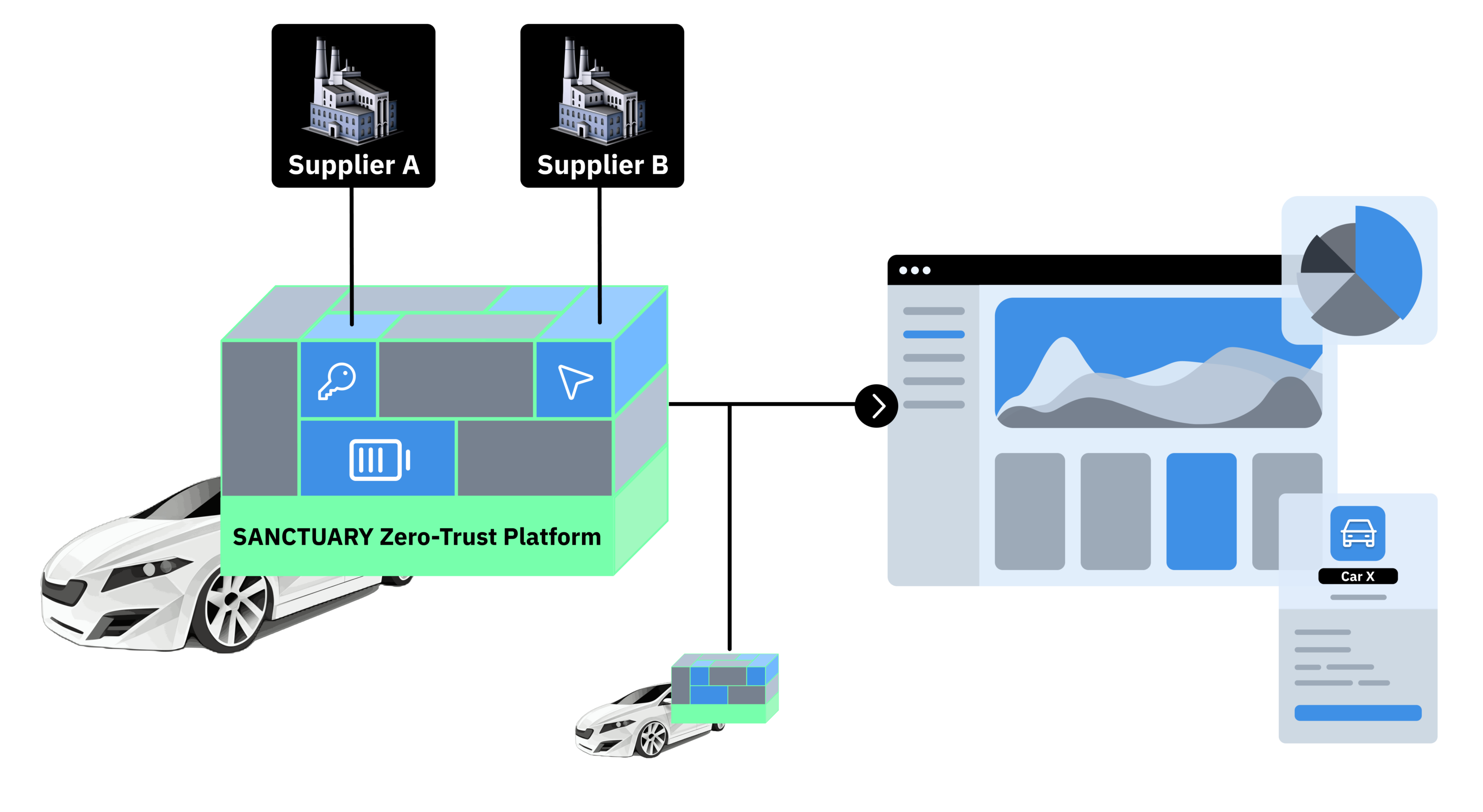
The complex software supply chain of today’s embedded devices forces vendors to rely on costly and inefficient compliance processes or to put blind trust in their software suppliers which increases the risk for cyberattacks.
The SANCTUARY Zero-Trust Platform strongly isolates software from different sources on the device. Moreover, the ZTP assigns secure identities to each software component such that secure communication channels between them can be established. In this way, the Zero-Trust Platform replaces the blind trust in supplier software with explicit trust relationships between components. The identities are not only used on the device itself, but also aid in the management of these devices via our fleet management dashboard. Our dashboard visualizes security-relevant information, performs remote system security health checks, and lets you plan rollouts of software updates.
Flexible Security - Even for Your Existing Services
The SANCTUARY Zero-Trust Platform strengthens security and reliability for complex software stacks on embedded systems while preserving the real-time characteristics of the system. The Zero-Trust Platform is legacy-compatible and can be easily integrated into existing ecosystems. Workloads can be bare-metal applications, real-time or regular operating systems, containers, and many more. Our tooling will not only set up all required (cryptographic) identities, but also assists in vulnerability/update management and conforming to regulations by creating a software bill of materials (SBOM) for your workload automatically. Once deployed, applications automatically benefit from the SANCTUARY Security Agent’s security services, such as our virtual TPM/HSM technology, remote verification of integrity and correct configuration, or more advanced health monitoring services.
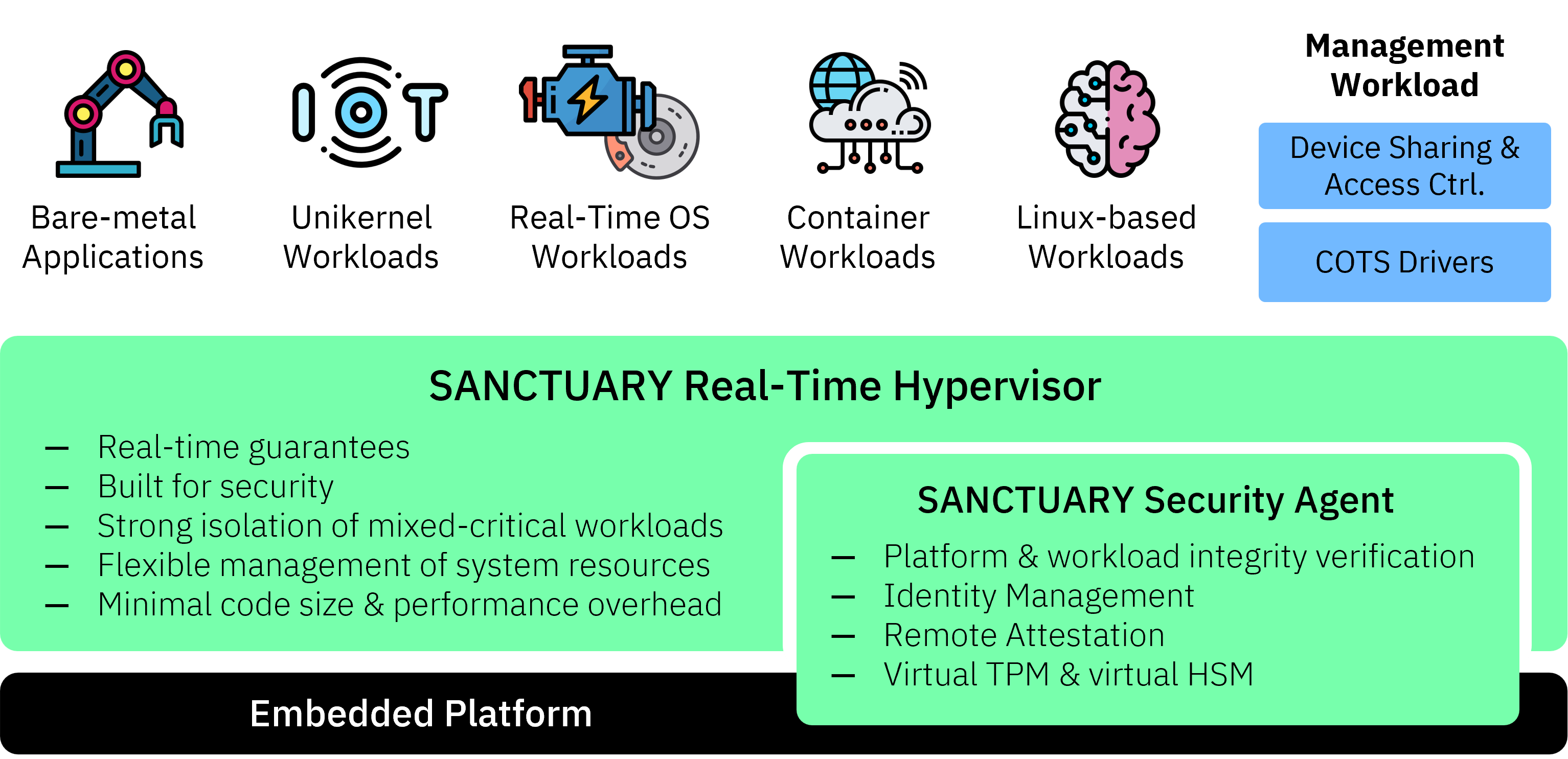
One Platform - Many Use Cases
The challenge of an increased software complexity concerns many industry domains in which embedded devices are used. Thus, the Zero-Trust Platform provides protection from cyberattackers in many use cases, whether its electronic control units (ECUs) in automotive, industrial automation devices like industrial PCs (IPCs) or IoT gateways, or even satellite systems.



The SANCTUARY Benefits
One Platform
One Platform
The SANCTUARY Zero-Trust Platform consolidates diverse workloads on a single unified platform which drastically reduces the complexity of multi-component embedded products.
Easy Service Migration
Easy Service Migration
The SANCTUARY Zero-Trust Platform supports existing software services without any modifications. Further, the SANCTUARY ZTP simplifies the development of new services by reducing the diversity of platforms in the system.
Cost Reduction
Cost Reduction
The SANCTUARY Zero-Trust Platform reduces hardware costs by aggregating multiple workloads on fewer devices and simultaneously reduces costs for development and maintenance.
